For example, many companies use a numeric keypad to secure entrance to a facility. To get into the facility, users must enter a valid combination to open the door.
Another example of physical security is the server room. Most server room doors are locked with a numeric padlock or a key. Higher-security server rooms sometimes even require fingerprint or retinal scans from anyone trying to enter the room. The benefit of locking your servers in the server room is a hacker cannot boot off a bootable DVD, which could bypass the OS entirely. After a hacker bypasses the OS, he typically can bypass a lot of the security by booting to a totally different OS.
A big part of physical security is locking doors to prevent unauthorized access to certain areas of the building, but in high-secure environments, that is not enough because of tailgating! Tailgating is when an employee unlocks a door and enters the facility, and an unauthorized person slips through the door with him. To prevent tailgating, the company should use a mantrap, which is two locked doors that someone must pass through to gain access to the facility. The hook is that the second door does not open until the first door is locked again. This allows the employee to be aware of who is entering the facility with him before unlocking the second door.
You can apply enterprise security best practices to your home systems. For example, to help secure your home system, you might want to prevent booting from a DVD so that an unauthorized person cannot try to bypass your Windows security.
BIOS/UEFI settings
You can set a number of settings in your system BIOS to help control the security of the system. Be sure to investigate the BIOS settings on your system to see what security settings you can enable on the system. Here are some popular BIOS/CMOS settings to aid in physical security:- Drive lock: Drive lock (a popular feature with laptops) is a hard disk specification used to protect access to the drive. To protect access to the drive, there are two drive lock passwords: a user password and a master password. The user password is used by the user wanting to access the system; the master password is used to reset the user password if the user forgets the password. Do not confuse drive lock passwords that prevent booting from the drive with the general CMOS passwords for the system. If the user password and master password are forgotten or lost, the drive is useless.
- Passwords: You can set a power-on password in CMOS to limit who can use the system. If the power-on password is forgotten, it can typically be erased via a jumper on the motherboard or by taking the battery off the motherboard and putting it back in.
- Intrusion detection: Most systems have intrusion detection features that can be enabled through the BIOS that will notify you if the cover is taken off the system. This is designed to alert you if someone opens the cover and takes internal components.
- TPM: The Trusted Platform Module (TPM) is a chip on computer hardware used to store cryptography keys that are typically used to encrypt data. A TPM chip can also be used to authenticate a device because it contains a unique key that identifies the chip, or hardware device. Most computers today have a TPM chip, and a number of software solutions (such as Windows BitLocker) can use the TPM chip to encrypt the contents of the drive.
Best practices
To protect your systems, follow these physical security best practices:- Secure server placement. Lock your servers in a room for which only a select few individuals have the key.
- Lock the workstation. When you leave your system, get in the habit of locking your workstation. A locked workstation can only be unlocked by you or the network administrator. This will prevent other users from accessing the system while you are away.
- Disable boot devices. Disable the ability to boot from a flash drive or DVD-ROM in the CMOS setup on the systems.
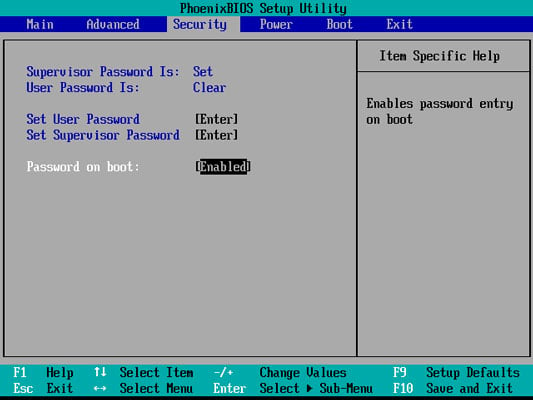
- Set BIOS/UEFI password. Because most hackers know how to go into the BIOS and enable booting from DVD-ROM, make sure that you set a password for gaining access to the BIOS/UEFI settings so that a hacker cannot modify your boot devices. The figure shows a BIOS password being enabled.
- Disable network ports. To prevent a hacker from entering your office, plugging into the network, and performing a number of network attacks, ensure that network ports, or jacks, in lobbies and front entrances are disabled unless an administrator enables them.
- Use a lockdown cable. Use a lockdown cable, also known as a cable lock, to secure laptops, projectors, and other types of office equipment to a table or desk. This figure shows a lockdown cable being used to secure a laptop. A lockdown cable usually connects to a special hole in the side of the computer equipment (look for a picture of a lock next to it).
Remembering ways to physically secure your systems will help you with the security portion of the A+ Exams. Be sure to place critical systems in locked rooms and lock down equipment that is accessible by the public.