Windows Server 2008 has a built-in event-tracking feature that automatically logs a variety of interesting system events. Usually, when something goes wrong with your server, you can find at least one and maybe dozens of events in one of the logs. All you have to do is open the Event Viewer and check the logs for suspicious-looking entries.
Using the Event Viewer
To display the event logs, choose Start→Administrative Tools→Event Viewer. This brings up the Event Viewer. The tree on the left side of the Event Viewer lists the various categories of events that are tracked:
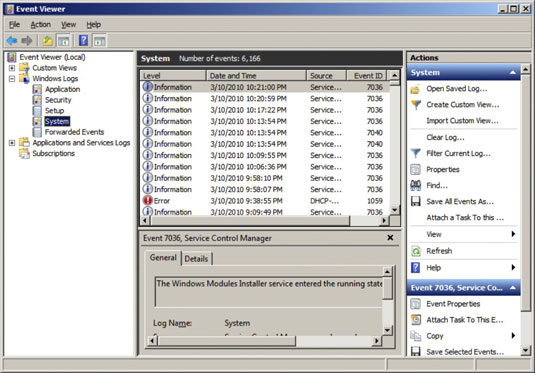
Application: Lists events that were generated by application programs. In most cases, these are events that the application’s developers purposely wrote to the event log in order to inform you of error conditions or developing trouble.
Security: Lists security-related events, such as unsuccessful logon attempts, changes to security policy, and so on.
Setup: Lists events generated during operating system setup.
System: This is where you find events related to hardware or operating system failures. For example, if you’re having trouble with a hard drive, you should check here for events related to the hard drive.
Forwarded Events: Lists other events that were forwarded to this server.
Note that you may find other categories in this list, depending on the roles you have configured for the server.
Select one of these options to see the log that you want to view. Notice the cute little icons next to each item in the log. The meaning of the icons is summarized below.

Information: This message simply indicates that some noteworthy operation completed successfully.

Warning: This message indicates that an event developed a problem that wasn’t fatal, but it may indicate a problem looming on the horizon.

Error: This message indicates that something has gone wrong.
To see the details for a particular event, double-click the event to bring up the Event Properties dialog box. Here you can see the details of the event. In some cases, you may be able to diagnose a problem just by reading the error message displayed in this dialog box.
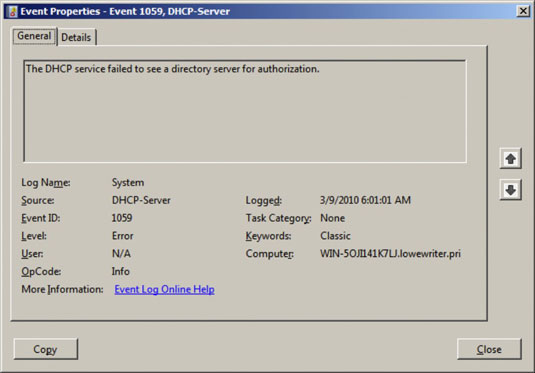
In other cases, this information just points you in the right direction — it tells you what went wrong, but you still have to figure out why.
Setting event log policies
You can set default policies that affect how application, security, and system event logs are kept by opening the Group Policy Management Editor. You can find the event log policies under Computer Configuration, Policies, Windows Settings, Security Settings in the tree to the left.
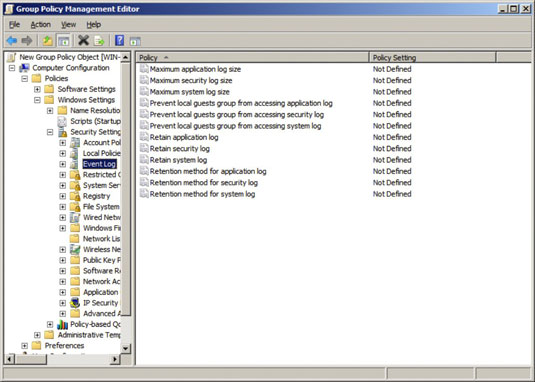
You can use these policies to specify the following options for the Application, Security, and System logs:
Maximum Log Size: Lets you specify the maximum size of the log in KB.
Prevent Local Guests from Accessing Log: Prevents users who are logged on using a guest account from viewing the logs. This is a good security precaution.
Retain Log: This policy sounds like it may let you disable the log, but it doesn’t. Instead, it specifies the number of days that log data should be kept if you specify By Days as the Retention Method policy.
Retention Method for Log: Specifies how log events should be overwritten when the log becomes full. Options are By Days, As Needed, or Do Not Overwrite.






