Data security, often also known as information security — and, in the case of securing electronic data, cybersecurity — concerns the protection of data and information assets that are used to store and process data. These assets can be paper-based, such as filing cabinets and hard copy documents, or they can be electronic systems, such as computers, databases, and software.
The data we collect, store, and process is constantly increasing, as businesses capture more data about more people, topics, clients, or staff. At the same time, the threats to data security are constantly evolving, from cyberattacks, malware, theft, and competitors to environmental hazards such as fire or flood.
To remain relevant and effective, your data security practices need to be part of an ongoing process of continuous improvement, as shown.
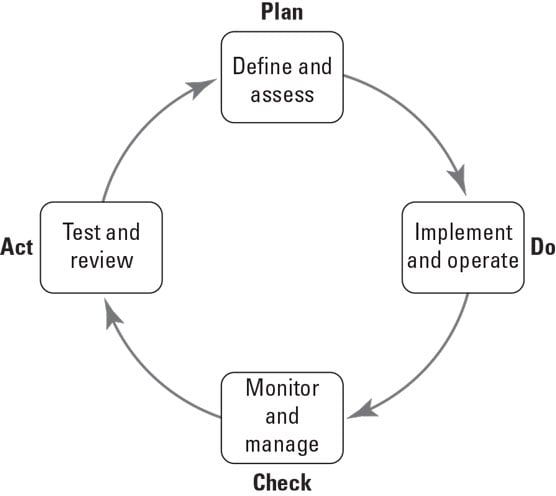 The continuous improvement process.
The continuous improvement process.If you’re reliant on third parties for data storage and/or processing functions, always check and verify their terms and conditions for the availability of their systems and services. This is particularly relevant when utilizing cloud- or Internet-based services that could impact your business operations.
Data security is often broken down into these three key areas, discussed next:- Confidentiality: Protecting data against unauthorized access, distribution, or publication
- Integrity: Protecting data against unauthorized modification, corruption, or tampering
- Availability: Protecting data against unplanned loss, destruction, or unavailability
Confidentiality
Confidentiality is about protecting data against unauthorized access, distribution, or publication. A key tenet of this concept is the need-to-know principle. Here’s a basic question to ask whenever you provide any individual or entity with access to data or data processing systems: Does this person have a genuine need to know?This question is particularly relevant when it comes to modern computing systems, where providing access to applications and databases to both internal and external parties must be carefully considered.
One way to manage such access is through the use of appropriate access controls and user privileges that limit or restrict the level of access and visibility of data within your systems to only that are required to perform specific roles. Such access should be based around the concept of “least privilege,” ensuring that users are not given more access than they need to perform their specific role or function. Users with enhanced privileges, such as system administrators, should not use their privileged accounts for normal, day-to-day work
Where you do need to provide access to data, it’s also worth asking whether the data needs to be provided complete and in its original form, whether you should cut it down by removing fields or elements or fields, or whether you need to consider pseudonymization, a technique that removes any part of the data that can directly identify specific individuals.
Confidentiality is also a key driver in the classification of data and data assets. Many businesses, organizations, and public sector bodies have specific guidelines on how they classify their data assets to ensure that need-to-know is enforced. It can also be used as a way of valuing data assets in terms of the impact to your business should the data be compromised or made public.
Integrity
Data integrity is concerned with protecting data against unauthorized modification, corruption, or tampering. Essentially, this means ensuring that the data you store and process is correct, accurate, and consistent over its entire lifecycle. You need to be in a position in which you’re confident that the data hasn’t been tampered with or compromised in any way as it moves from one system or individual to another.In many areas of business, data integrity is as important, if not more so, than confidentiality. Imagine for a moment you were buying something online. You need to have complete confidence that the value of pounds, euros, or dollars you paid is the same that arrives with the seller at the other end of the transaction for your purchase to be completed. This is data integrity at work.
Key approaches when considering data integrity include
- Validating data inputs and data outputs: This involves ensuring software and applications only accept, produce, or respond to known good inputs and have strong error handling and validation routines.
- Protecting against system or hardware failure: Calls for deploying systems on high-availability — resilient or cloud-based platforms that reduce single points of failure, in other words.
- Using encryption to protect data transfers: This involves using appropriate technologies such as Virtual Private Networks (VPN) to safeguard the data being transferred, and/or Transport Layer Security (TLS) to encrypt the traffic end to end.
- Implementing safeguards that reduce the likelihood of human error: Steps here could include having supervisors double check sensitive operations that staff are undertaking.
Availability
Availability entails ensuring that data and data processing systems are available when they’re needed. Imagine going to the bank to withdraw money. You reach the bank teller and are informed that, unfortunately, the bank systems are down and your request cannot be processed. That would be frustrating, wouldn’t it? If you need to withdraw cash from the bank, you don’t want to hear, “The systems are down and will be unavailable for the next 28 days. Sorry for the inconvenience.” You need your money now, not in a month’s time!Ensuring that access to data and data processing systems is there when users need the data is essential for most businesses. Some key elements for consideration include
- Backup and recovery solutions for data, files, systems, and applications
- Disaster recovery (DR) and business continuity planning (BCP) that detail how your business will handle a major issue that impacts operations
- High-availability and cloud-based solutions that show how you achieve resilience in data storage and processing systems
- How you will manage the impact of environmental factors (such as fire and flood) or other security incidents
- How resilient your systems are to disruption and can whether they can continue to operate under adverse conditions, such as those caused by a security incident or technical fault

