As a pen tester, you need a solid understanding of how an attacker can access your systems and how they can conduct attacks. You also need to know about security vulnerabilities as well as penetration testing tools, techniques, and skills that today’s most elite pen testers use on a daily basis to conduct penetration tests that keep their company’s assets safe.
Skills needed for penetration testing
You’re going to need a wide variety of skills throughout your pen testing career, but the biggest (or most important) skills to have are in the realm of networking and general security.To be able to conduct a pen test with any amount of confidence, the more you know about security and network architecture, the better. For example, to run a basic pen test, you need to enter a network address or subnet range in your scanning tool.
You need to also know the difference between vulnerability scanning and penetration testing and why they’re similar and how they’re different. The following image shows the basics of setting up an IP addressing range to scan and identify vulnerabilities. After you know the risks and weaknesses, you can them move into the details on how to exploit (pen test) what has been found so you can learn whether the technology is secure.
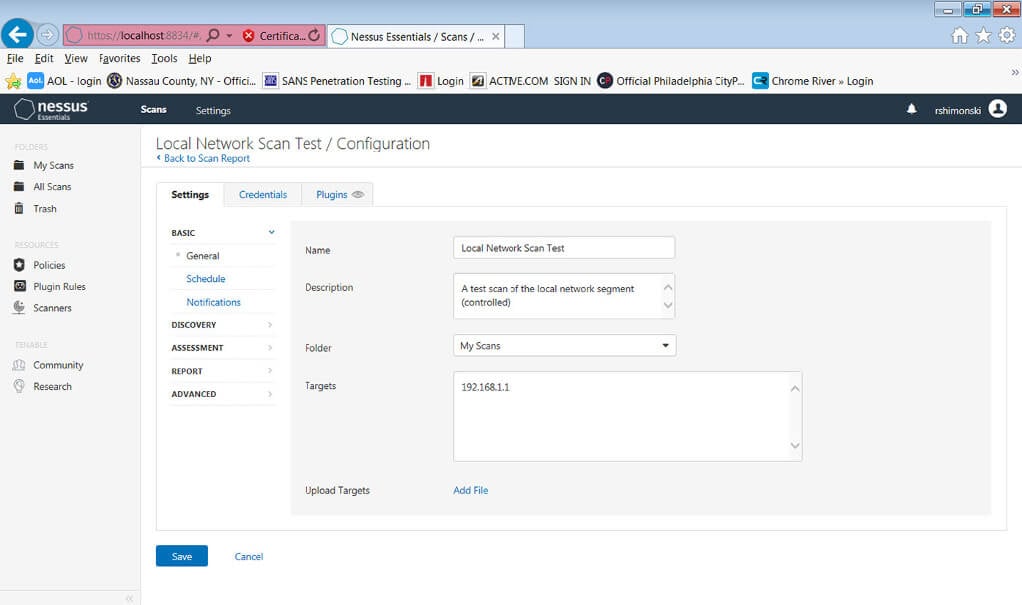 Adding an IP range to scan
Adding an IP range to scanIt’s also crucial to understand IP, protocols, networking, and other technologies related (and also not directly related) to security analysis because as weaknesses are identified (perhaps with a scan), then you can then move to exploit them (pen test) no matter what technology you’re presented with (database, mainframes, virtualized systems, for example).
No stone is unturned as a pen tester and what you need to expect is everything and anything. You are tested just as much as the systems you’re testing. Additionally, criminal activity isn’t confined to computers. The Internet of things (IOT) is an ever-expanding network of connected devices that includes, but is not limited to, tablets, phones, and smart home devices such as TVs and thermostats.
You may not encounter all those devices working as a professional pen tester in the corporate world, but you need to be aware of all connected devices. And when you’re pen testing, take time to find out which devices could be affected, such as mobile devices and assets used by field staff.Also be aware of a hacker’s reconnaissance procedures. Hackers often begin attacks by using general research techniques, such as Internet searches that point a hacker in a direction, to learn more about accessing your company. For example, a simple Whois search might provide an address. A DNS search or query could provide a clue. Google searches may help to identify paths of attack, URLs, domain names, IPs, email addresses, and more.
Basic networking
Basic networking includes, but is not limited to, understanding the OSI (open systems interconnect) model. Knowing how data transits from one location (a sender) to another (a receiver) is key to being able to unwind how many attacks occur.It also includes knowing how routers, switches, hubs, load balancers, firewalls, intrusion prevention devices, and other network black boxes on the wire work. (Black-box security testing refers to testing software security from the outside in. Generally, the tester has little or no knowledge of the internal workings.) If you pen test a router, you need to know how it operates.
The TCP/IP protocol suite also falls under basic networking knowledge. The transmission control protocol (TCP) and Internet protocol (IP) controls how computers connect to the Internet. It includes many of the protocols in the 7-layer OSI model.
The Open Systems Interconnection (OSI) model is used as a logical framework to show how data travels from the source to the destination and back to the source through the many technologies that comprise the network, systems, and applications. It’s a model of standards that shows the under the hood actions of the technologies at each layer.
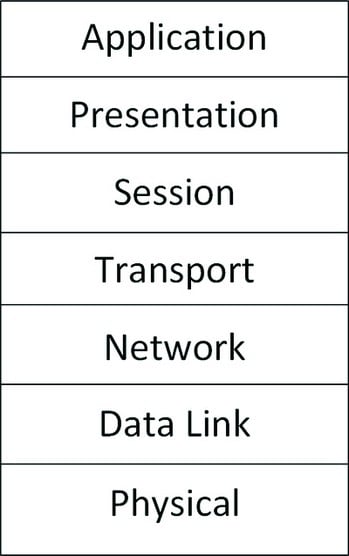 Examining the OSI model
Examining the OSI modelThe protocols used in a suite (such as TCP/IP) map to the various layers of the model and perform different functions. For example, FTP operates at a higher layer in the model than TCP or IP. The theory is that, if the lower layers don’t work, then the higher layer protocols won’t operate correctly. The OSI allows you to troubleshoot problems in a workflow manner.
The image below shows a wire packet capture that shows a lot of the information you need to read through to conduct a pen test with a tool such as Wireshark. Here you can see packets that when captured can be decoded to tell you the details within them.
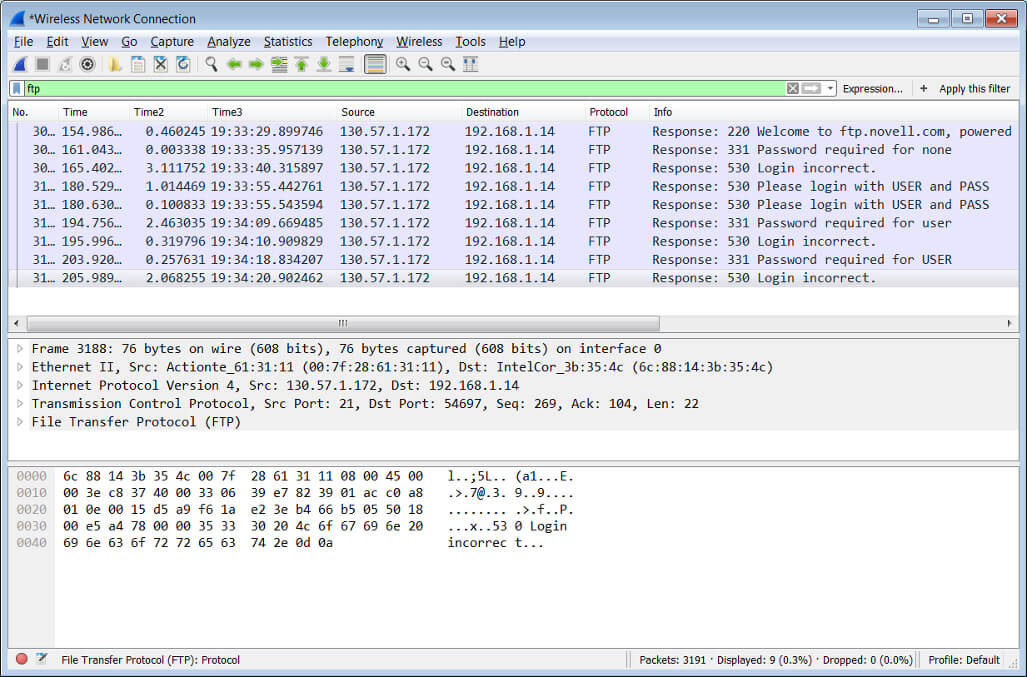 Digging into a network packet capture
Digging into a network packet captureHaving knowledge of these protocols, how and where they operate, and what is contained in the frames, headers, and other inner details of the packet is what will make you a great pen tester. If you run a pen test and it reports back, for example, that you have a vulnerability in telnet that’s sending packets back and forth in cleartext, you need to determine what path a hacker may take.
You can more easily make that determination if you know how the protocols work and what is expected behavior and what can be manipulated versus what could be impacted by a software bug. This way, you can test it yourself first to identify whether you have an issue that might need to be remediated or mitigated.
If you want to be a great pen tester, you should study more on TCP/IP. It’s the main protocol suite in use today across the world; when it was first put into production many years ago it came with many flaws. Its ease of use is one of the biggest flaws and the fact that security was an afterthought behind usability.
Although today’s networks and systems can account for these flaws, there is always danger in the shadows. Study TCP/IP and all of its sub-protocols and how they work to get better at testing weaknesses in your enterprise.General security technology
In the general security technology category are firewalls. Most scans against devices such as a firewall turn up little to no information. Knowing why is helpful to your report. For example, in a ping sweep, you ping the interface and find nothing because the firewall has disabled that protocol that responds.The image below shows a Cisco router firewall log that lists the source and destination IP addresses used to make each connection as well as a description of what that connection did.
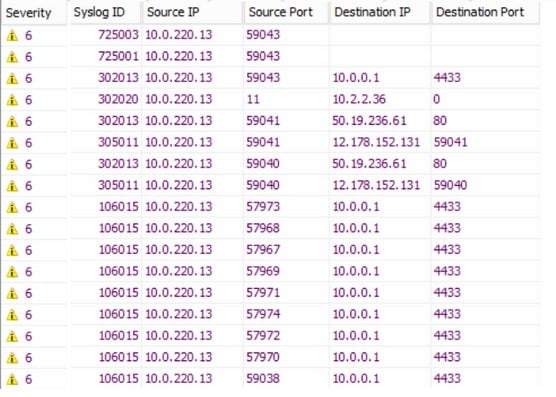 Review a firewall log.
Review a firewall log.Another example is when you run a scan and find open ports are in use on a web server in a DMZ behind a firewall that shouldn’t be. By examining the firewall log that sits in front of these servers, you can see what the source IP address is that’s attempting to make those connections. You can detail it as an active attack and prioritize it immediately to patch or fix.
Other general yet important technologies to consider would be devices such as intrusion prevention and detection systems, load balancers, access control lists (ACLs) on routers and wireless access points, controllers, and mobile extenders. Each and every one of these devices all can be exploited and the more you know about them and how to review the logs on them, the better you are at identifying risks and conducting ethical hacking.
Systems infrastructure and applications
You must also be familiar with a company’s systems (servers, storage, and telecommunications) and the applications that run on them. This includes operating systems and the services they offer (name resolution services, remote access gateways, and IP address leasing). Pen testing any and all these areas will show up on your reports.If you run a scan on a Domain Name System (DNS) you may find that it needs to be patched. If the server is a Microsoft Windows Server system, you may be able to download needed patches and apply them based on the report.
You may also be running a UNIX or Linux system running BIND, which is a DNS name daemon or service. Either way, both may show up on your report as needing attention. Knowing what they are can help you to direct attention towards not only how to repair them, but also which must be prioritized immediately.
Web applications and web programming are also major areas that are exposed to vulnerabilities based on the logic needed to keep them running. Database servers running the Structured Query Language (SQL) may be subject to injection attacks. Operating systems that the services and applications run on also remain open to attack and need to be scanned and patched.
Mobile and cloud
Mobile technology is also a must-know endpoint technology quickly replacing the desktops and other devices. They also travel to and from locations and absolutely must be addressed, whether the devices are company assets or company software and data used on a personal device. There are challenges with this system, which mobile device management (MDM) solutions help overcome.You might worry about testing them to make sure they’re secure, but you approach this like you approach all the other systems you’re accountable for — you scan, test, and report based on your findings and handle the risks as you identify them.
Cloud is another boundary IT security pros are trying to cross in the world of security and pen testing. Because cloud technologies fall under the purview of their cloud provider, as long as you’re working in conjunction with the cloud provider’s security team and they’re conducing pen tests, then you have achieved the same goal as if you did it yourself.
You might face the fallout of mistakes or mishaps committed on the vendor side.
Penetration testers need a wide variety of skills and knowledge, but they are essential to helping ensure the security of our IT infrastructure.
