Unfortunately, in many businesses, IT gets a bad rap; security experts are often perceived as barriers to progress, because people who just want to get things done, such as adopting a new CRM software solution, often have to wait for IT’s approval.
IT is there for a reason. Respect that team and what they do, and look for ways to team up with them to establish reasonable policies for securing data, controlling how data is used, and restricting access to mission-critical software. Reasonable policies are those that address IT’s security concerns without excessively inhibiting progress.
Securing your data
One of IT’s main roles is to protect your data. This data may be internal, such as emails, shared files, customer data, or financial information. IT also protects your external brand from being compromised, such as preventing hackers from hijacking your website or social media.With many stable cloud-based software providers available, it’s easier than ever for your employees to open an account and upload your company data to a vendor’s server. Your IT staff has fits, because it places the company’s data on a system that IT has no power to protect. How secure is that vendor’s network? What happens if that vendor gets hacked? Will it sell your data? All these questions must be answered before you choose a vendor, and they all need to be asked by someone who understands IT.
Work with IT to create a data security policy and make sure everyone in your organization understands and abides by that policy. As a business, you never want to lose control of your data, and that control starts with employees being responsible about how they store and share that data.
Your security policy should, at a minimum, include this information for your team to reference:- Are team members allowed to install software on their computers?
- Can employees create and use accounts with Software as a Service (SaaS) providers?
- What data can be uploaded to any cloud-based services, such as Dropbox or Google Docs, and if it can, which services are employees permitted to use?
- Can personal portable digital devices (such as smartphones) be connected to company networks? If so, what software can they use?
Controlling access to data
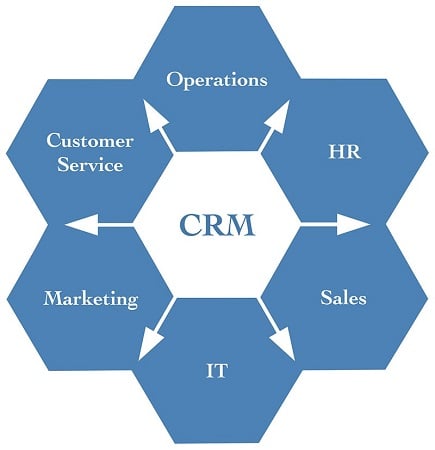
Your employees must understand that the data you collect is the lifeblood of your business. Unless everyone shares responsibility for stewardship of that data, it will get out. All employees need to understand how data is accessed and used throughout everything each employee and team member does. The more data you have and the better it’s organized, the more powerful it is; be sure your team respects that power.The image below shows how everything is interconnected in your organization, and highlights the central role that IT plays in controlling the way the information is transferred between departments. Be sure someone is in this central role, even if your organization is too small to have an IT professional. While the goal of a CRM is to break down data silos and enable information sharing, from a security standpoint, you want to have control over that sharing.
Start with how and where data is accessed. If you have an IT department, it probably installed software on each device and computer to protect it. But that doesn’t necessary protect everyone. Make sure that everyone connects to your network with a virtual private network (VPN) when connected outside your office with unsecured Wi-Fi. Make sure employees know to never plug in strange USB devices into their computers.
If people have access to data in the form of a portable file such as a spreadsheet or a word-processing document, make sure they only upload those files to systems that you approve. If they’re using cloud-based software, be sure you understand how that software works and if your data can be shared.
Controlling access to your CRM software
Multi-user access to data is absolutely critical to your business. Not everyone in your company requires access to all the data that your company has and uses.CRM software is a powerful tool with access to a great deal of sensitive data and the power to broadcast marketing content globally and almost instantly. Given its power, you must consider who really need access to which parts of your CRM. You don’t want an intern with the ability to send an email broadcast to your client database without approval.
Fortunately, most CRM software platforms include features that enable you to restrict access to certain features or to certain activities, such as posting content or looking at customer data. You can create separate, password-protected user accounts and assign privileges to users individually.
Never permit users to share a login. If you do, you lose the ability to track individual user activities and hold each user accountable for what he does. If the CRM solution charges per user, then budget for separate user logins; don’t try to save money by allowing users to share a login. You can also look for a CRM platform that doesn’t charge per user.